- Unlimited Leave
- Posts
- The case for AWS Multi-Org
The case for AWS Multi-Org
along with other predictions for re:Invent
Oh boy oh boy! We made it through the noise of Black Friday promos.
It is here. Unlimited Leave. The weekly AWS M&G newsletter you can snooze in your inbox for two days to read while on your flight to Las Vegas.
That's right. By the time you get this email, there are less than 48 hours until you can pick up your badge and start collecting all of that wonderful swag. I can hardly contain myself.

Here in the states, I plan on coming out of my food coma long enough to overspend on consumer goods and drift back to sleep until 3 hours before my flight boarding time. How are you going to pass the time?
I bet if you knew Professor (Sherman) Klump you'd ask for a little bit of that experimental formula to erase the damage you did yesterday. I know I would.
But that's in the past. Let's look at whats in store for the future.
This week's topics
As promised. My case for Multi-Org
Where I'm eating and drinking for free this coming week
Some predictions for re:Invent
Latest M&G Announcements
Resource of the week: AFT SSO Account Configuration
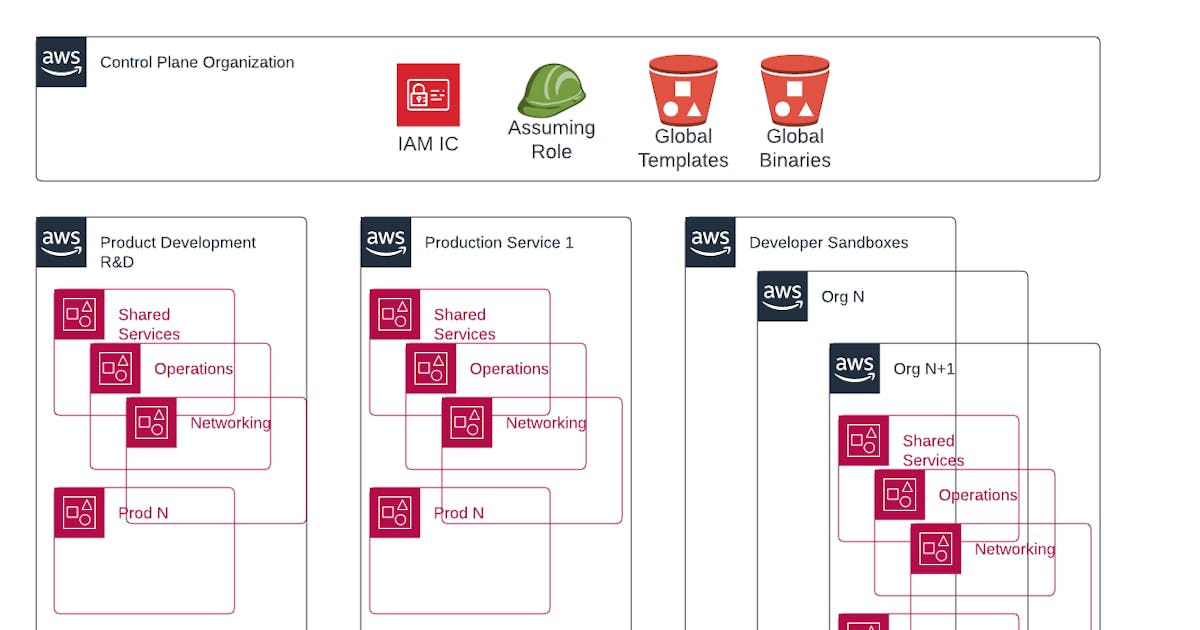
My case for AWS Multi-Org (start preparing now)
Earlier this week I posted 'The case for AWS multi-org`. It's the primary reason you should have saved this email for your flight... This post feels like the longest I've written*. I don't know if I'll do that again.
*This is the last week I will run this poll.
It is currently head-to-head for Option 1 vs. Option 3.
I don't think I can provide as much value with multiple posts like ☝️ but I don't mind putting one together every couple of months when the topic fits.
Please provide your feedback. A new poll will start in the next couple of weeks to determine how to implement any changes.
Hors d'oeuvre
Aside from the one free drink that I'll get before I blow all my per diem at the tables, I'll be bouncing around to a handful of events and meet-ups throughout the week.
Some meetups are social events and others are community focus groups or round tables.
There are of course all the evening receptions that Amazon hosts in the vendor hall. That must be the only way each vendor can get 20k+ badge scans over the course of the week.
Monday
DoD Tech Day (If I can get there in time)
Monday Night Live
Tuesday
AWS IQ Expert Round Table
AWS Customer Council Meetup
AWS Community Builders Meetup
Wednesday
re:Invent 5k
Service Catalog Focus Group
TBD Pub Crawl Locations
Thursday
AWS Global Security & Compliance Acceleration Forum
AWS Certification Appreciation
and obviously re:Play
I'm nowhere near a geeky celebrity but if you somehow run into me and recognize me, please say hi. I'd love to hear what your M&G pains are and if you have time, what your thoughts are about the newsletter and share some 🍻.
As always, if you'd like to link up for a chat sometime during the week, you can message me in the AWS re:Invent 2022 Slack.
Some predictions for re:Invent
My focus is and always has been governance at scale. How can I or the team enable developers to do their work without worrying about all the little stuff like monitoring and log collection? Awfully boring stuff if you ask most developers working on programs that actually generate revenue.
Over the years, service releases or feature enhancements for AWS services that help better-enable governance at scale don't get a lot of fanfare. If I had to guess, I'd say 75% of the architects in AWS are building applications and services while the other 25% are focused on Management and Governance.
To me, building out AWS Organizations and Accounts is like building the product. The architecture of the accounts is just like the architecture of a full-stack application if you look at it through the right lens.
That is why I think this year there is going to be more attention given to Services, Features, and Reference Architectures that support the management and governance of Multi-Account and (if they don't flat out say it) Multi-Organization Strategy.
Managing Accounts
A few issues ago I mentioned some big updates for GovCloud. This is just the tip of the iceberg. Expect more updates to Control Tower and even more specifically Control Tower in GovCloud. Like the ability to display the compliance status of external AWS Config Rules.
Reference Architectures such as the Account Factory for Terraform and Customizations for Control Tower have their own space in the AWS Control Tower User Guide but most don't go that deep into the docs for deployment. They are usually provided as optional frameworks and likely only deployed based on a recommendation through your AWS Account Manager or SA if you are lucky enough to have those.
Having deployed both of these solutions many times, you can see the power in them. You can also see the value AWS would gain by nudging more customers to use them. Today, they require a little bit of front-loading to deploy to an organization. They don't currently integrate with the console, CLI, or SDK. I expect to see either of these solutions incorporated into the backend for features added to the console and CLI. If not these exact solutions, then something that is built off of their foundation.
Service management Delegation
With recent updates like Delegate Organization CloudTrial Administrator, you have to know there is more going on on the backend around service delegation. Getting anyone and everyone out of the management account is crucial. I think everyone sees the benefit here.
I have my gripes over how some of the services have been delegated or how you can use them across the org from the delegated account. Some of it is growing pains from AWS. Some of it is me just learning the intended purpose in mind for the delegation. And as I stated in a previous issue, I may just be flat-out doing something wrong.
I expect this list of Services that work with Organizations to grow or change slightly with regard to what services can be delegated to an administrator account and why.
If you read my Case for Multi-Org by now, it would be a stretch, but we could maybe see delegation outside of the current organization.
Automated deployment
All of these new management and governance services/features are great, but the issue of scalability hasn't been addressed. Not for account orchestration or for application deployment. Obviously, I'm more focused on account orchestration.
The suite of AWS Code(Build/Commit/Deploy/Pipeline) services is probably great for application deployment. Admittedly I don't have much experience with them but I know enough to tell cross/multi-account deployments aren't trivial.
If you've looked at Account Factory for Terraform, you can see that the solution incorporates GitHub, GitHub Enterprise, Bitbucket, and of course CodeCommit.
Expect more of this.
Customizations for Control Tower rightfully leverage the AWS Code* suite of services, but again, keeping your customizations up-to-date or in sync is not trivial.
While the solutions that might be coming down the pipeline probably won't directly support the Governance and Management of multiple accounts or organizations, I do suspect we will see some releases of features or services that better support multi-environment and/or account deployment and management of delivery pipelines.
Latest M&G Announcements
I already mentioned AWS Control Tower now displays the compliance status of external AWS Config rules but I don't get too crazy with custom rules. I do use Config Conformance Packs to validate that deployed resources are present.
This is big - AWS Service Catalog now supports the sharing of principal names when sharing a portfolio within an AWS Organization which at first glance doesn't look like that big of a deal. The IAM Principals still need to be present in the account but if you deployed Service Catalog Portfolios in the past, someone needed access to give the users/groups/roles in the account access to the portfolio. That or you need a wacky custom resource to do the assignment. If I read this right, that is no longer required. The roles just need to be in the account. And obviously have the permissions required to both see/use the portfolio and products as well as launch the resources deployed by the product. I'll be playing with this more soon.
I'm more annoyed about the AWS Organizations CloudFormation resource type than I am excited. At this point, I'm not even sure how I would implement it with. The only thing I can't do with the frameworks I have in place is create/manage OUs but those are static enough and already need to be enrolled into Control Tower. This definitely has value for Control Tower laggards.
You can now more easily provide proof that you haven't been doing your job very well and lying about it with query filters in evidence finder for AWS Audit Manager.
Finally, because no one has actually launched Control Tower in GovCloud since becoming GA a month ago, here is an AWS walk-through blog post on how to use AWS Control Tower to simplify your multi-account governance in AWS GovCloud regions.
AFT SSO Account Configuration
If you have started using Account Factory for Terraform as your account provisioning and customization tool, this solution is a must-have.
I retrofitted the bootstrap for the last 4 AWS Organizations I deployed and this global customization makes it so easy to assign permission sets to users and groups immediately at account provisioning.
The best thing is it is idempotent. In that, if someone changes permissions elsewhere, the next time you trigger the customization pipeline on the account, your permissions will be reset to how they are configured in the account request module.
I'm working on a scheduled task to run all of my AFT Customization Pipelines daily.
Help us grow
Attending re:Invent in person?
There are a few hundred of you active here, some of you have to be going to re:Invent right? If you see one of these laying around:

Snap a pic of it
hand it to a colleague/friend to subscribe or leave it behind for the next stranger
Tweet the pic to @unlimitedleave and follow us
or reply to this email with the pic
Be entered to win some AWS Credits or something I haven't thought of yet.
Attending virtually?
Rather spend the holiday with your in-laws than the Junior Architect you just hired?

The In-Laws (1979)
Help everyone out by forwarding them this email or tell them to subscribe 👇